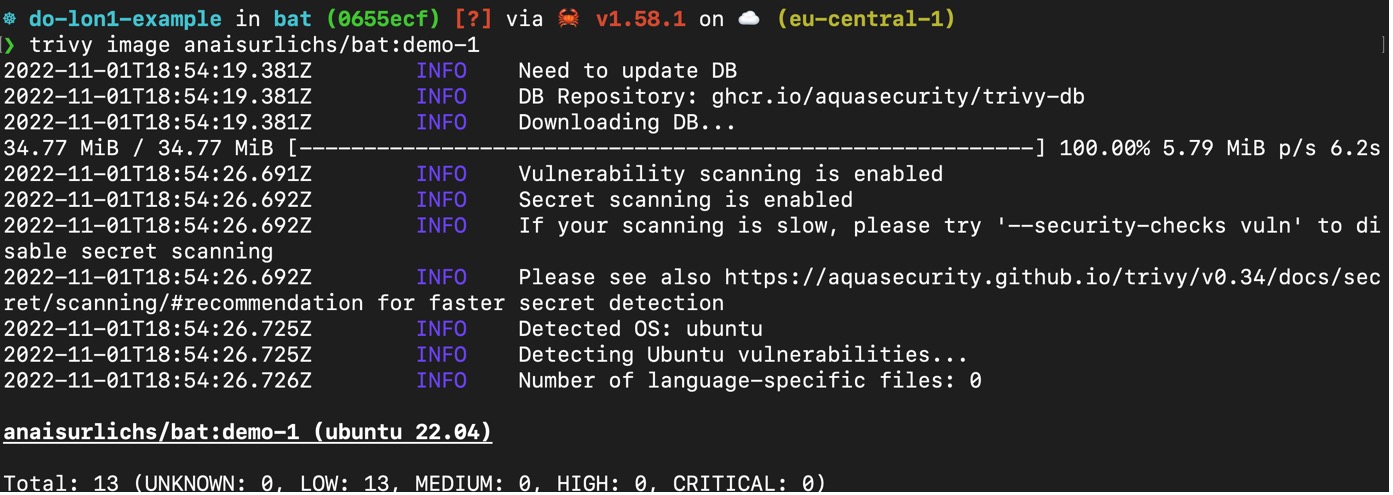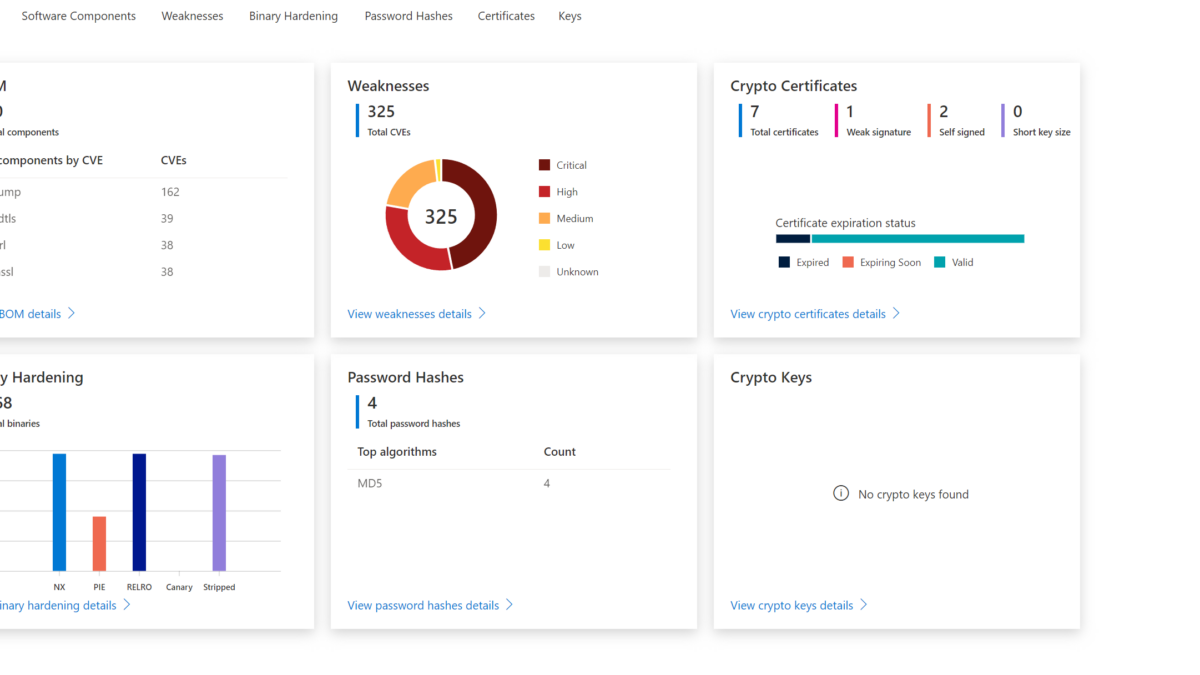
How to use Defender for IoT firmware Scanning for checking potential security vulnerabilities and weaknesses

Binary Authorization | Google Cloud | by Prasanna Bhaskaran Surendran | Google Cloud - Community | Medium

Guard against security vulnerabilities in your software supply chain with Container Registry vulnerability scanning | Google Cloud Blog
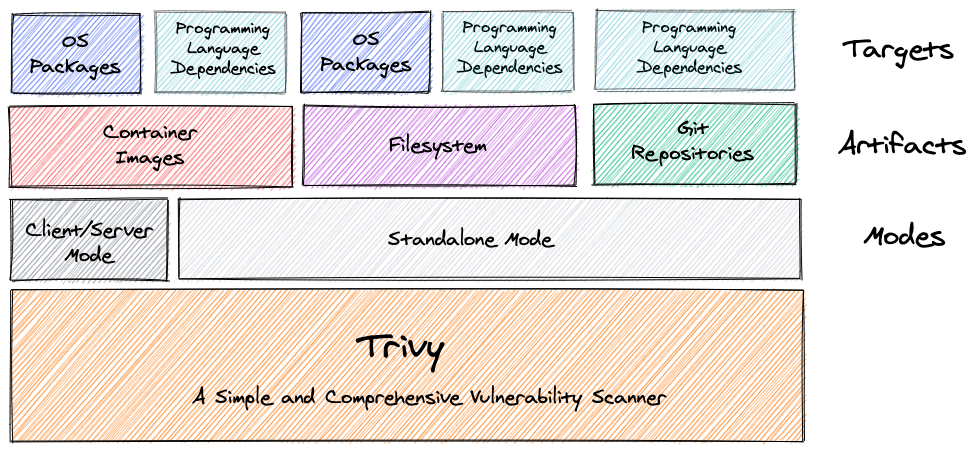
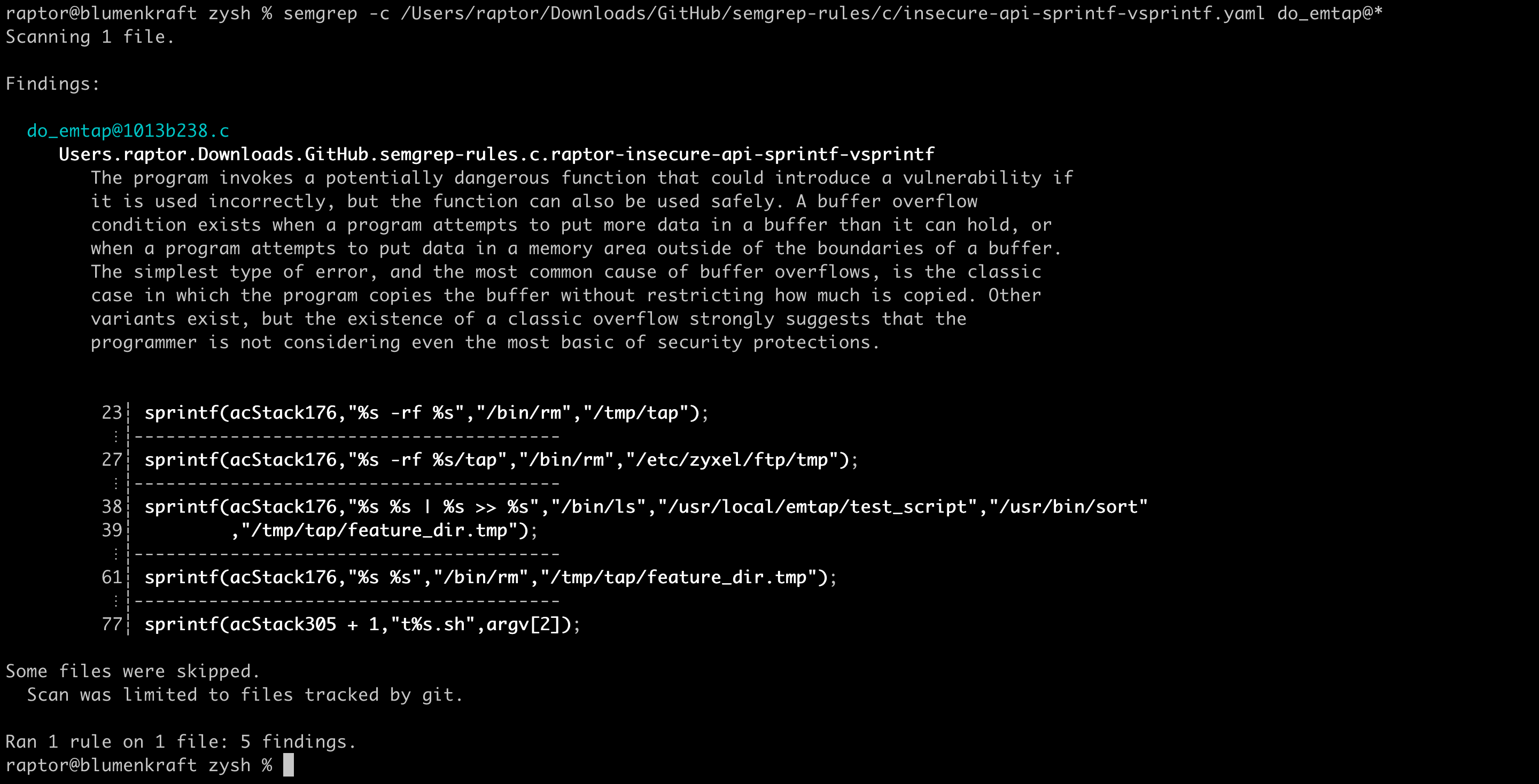
GitHub - intel/cve-bin-tool: The CVE Binary Tool helps you determine if your system includes known vulnerabilities. You can scan binaries for over 200 common, vulnerable components (openssl, libpng, libxml2, expat and others),

ANZ uses Google tool to enforce security on containers and code - Finance - Cloud - Security - Software - Projects - iTnews

Implementing Binary Authorization using Cloud Build and GKE | Cloud Architecture Center | Google Cloud





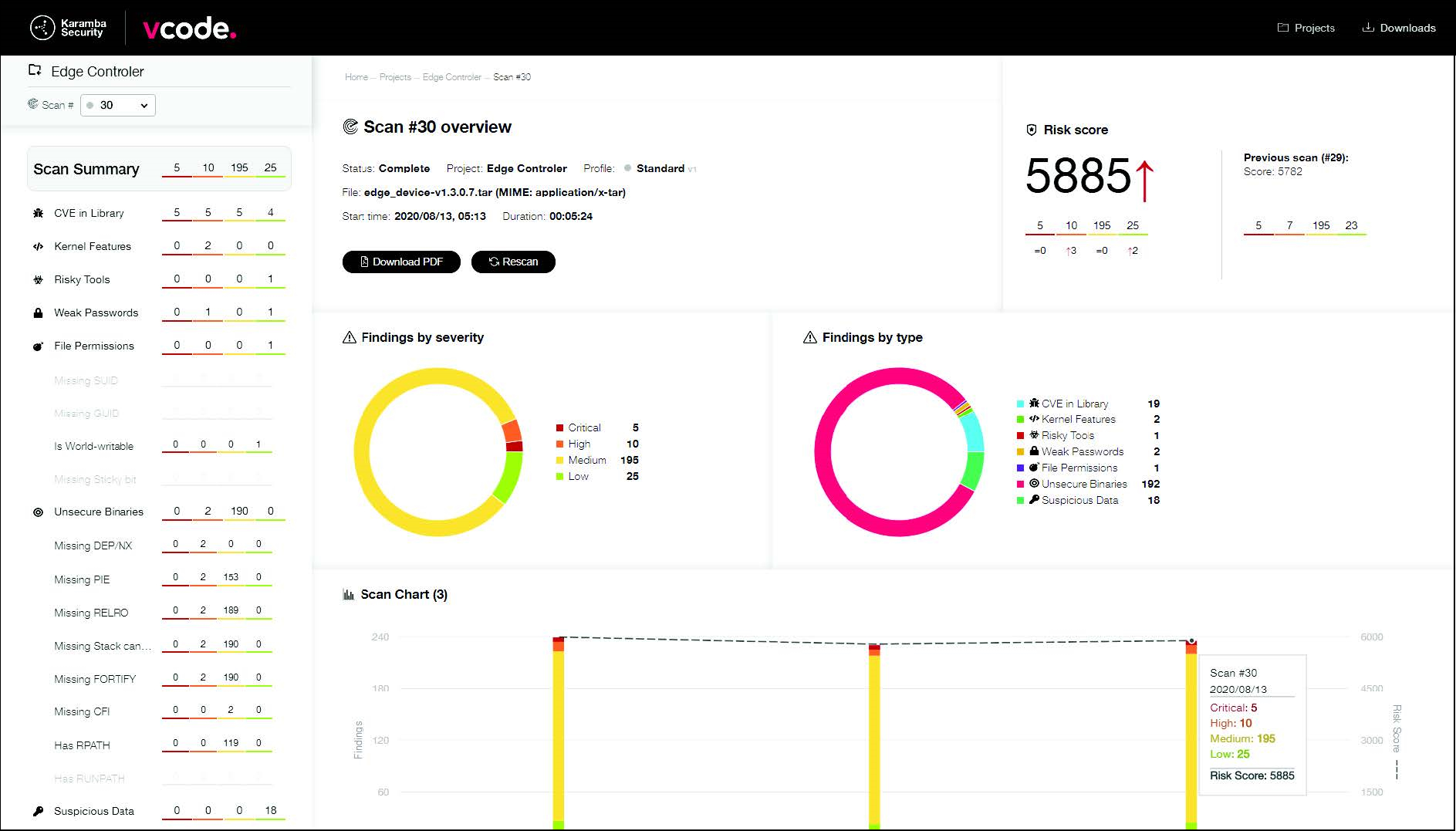




.jpg)