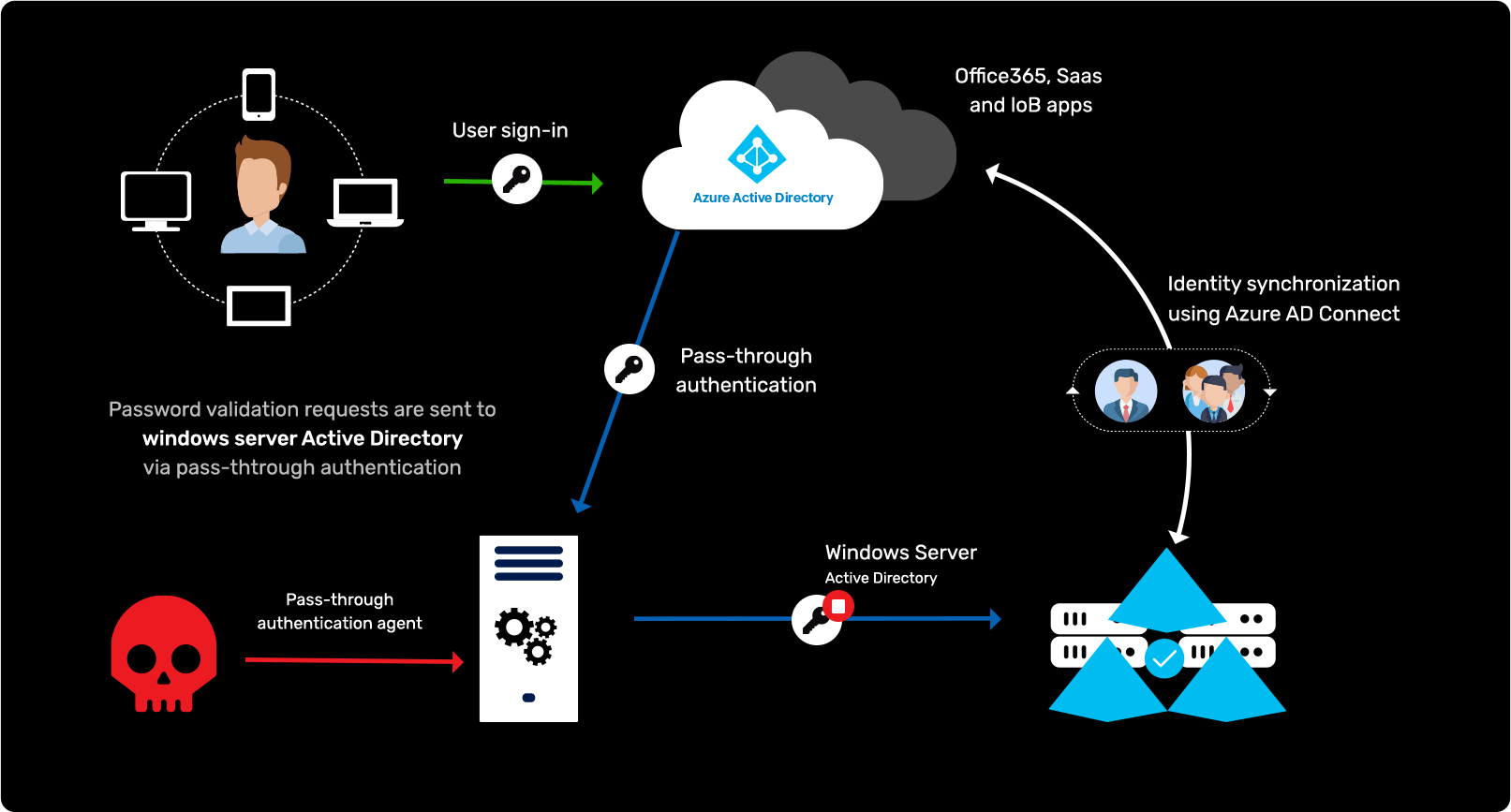
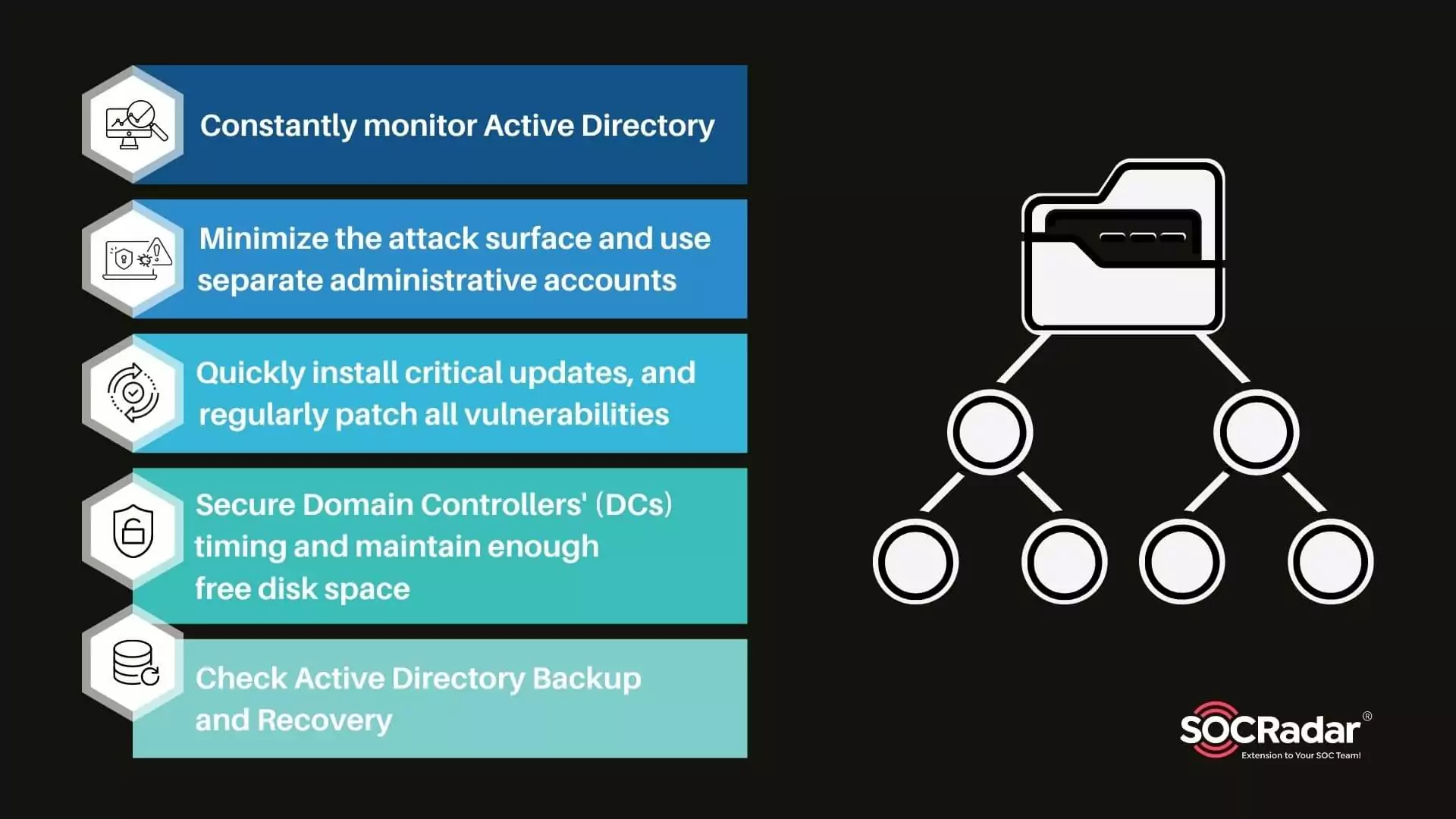
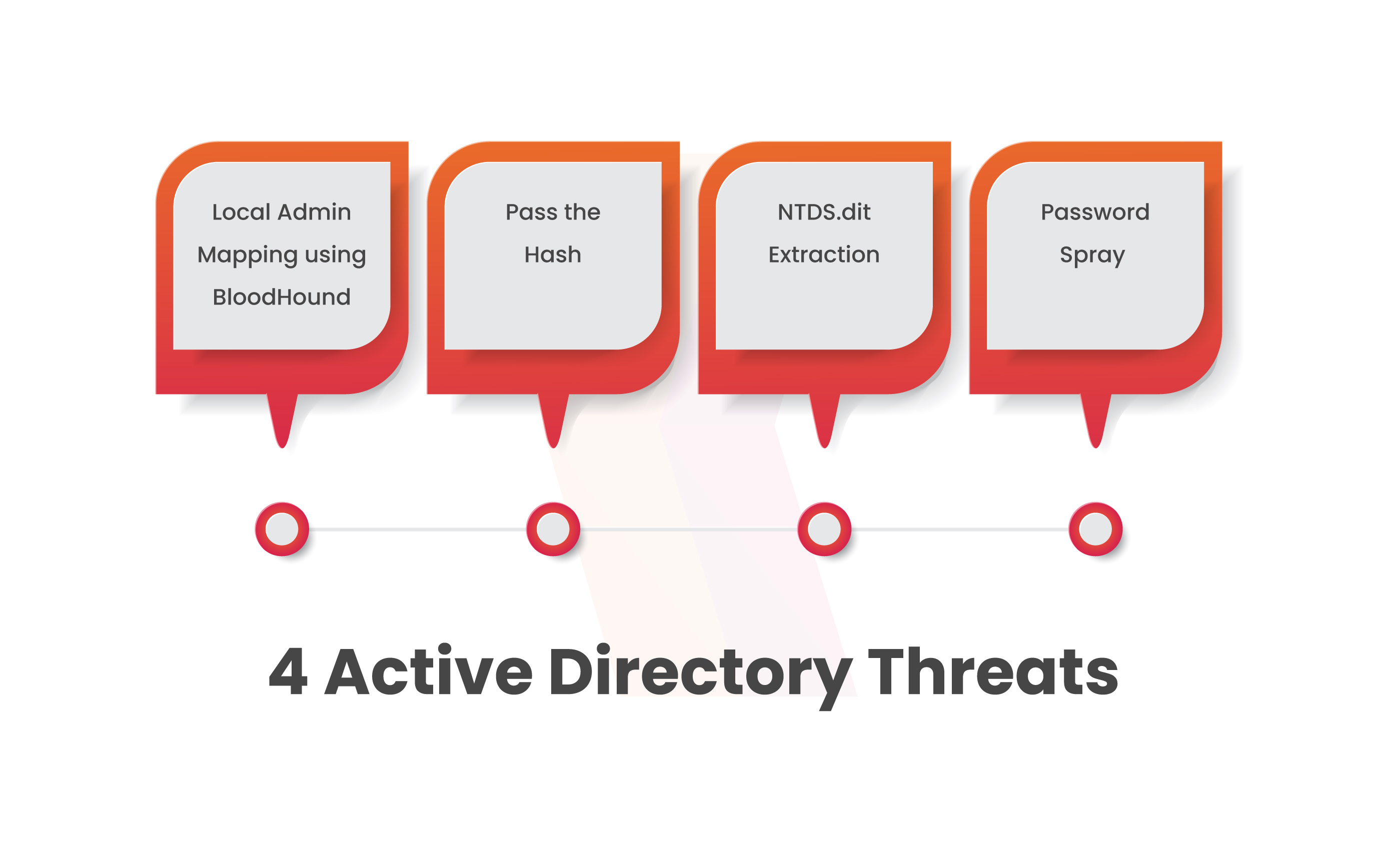
GitHub - infosecn1nja/AD-Attack-Defense: Attack and defend active directory using modern post exploitation adversary tradecraft activity

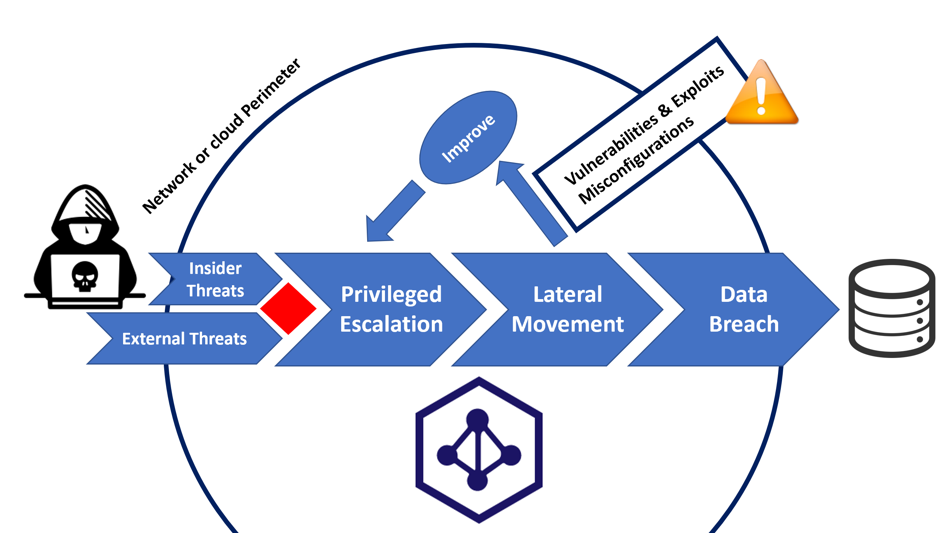
Chaining together Active Directory attack techniques to give your organization the edge against attackers | XM Cyber







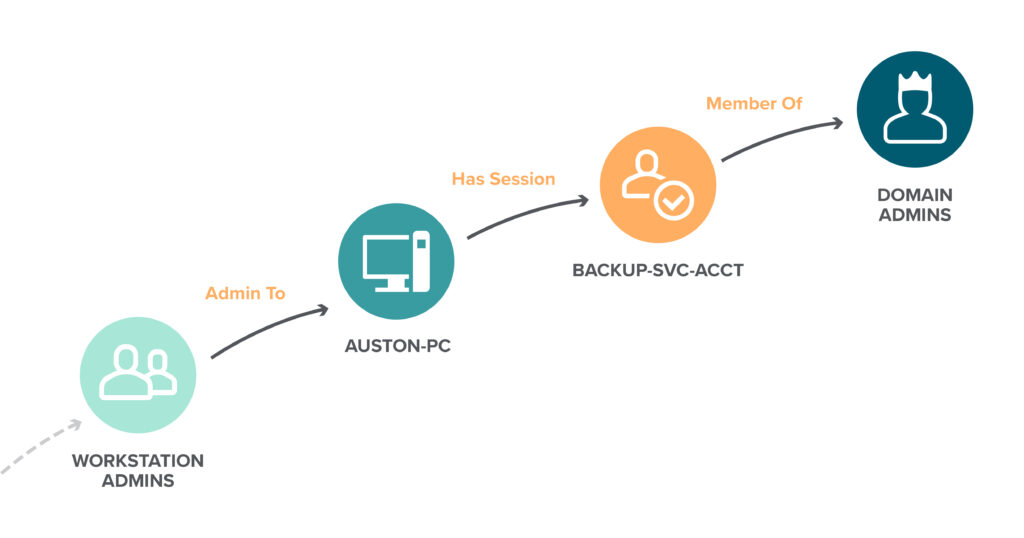


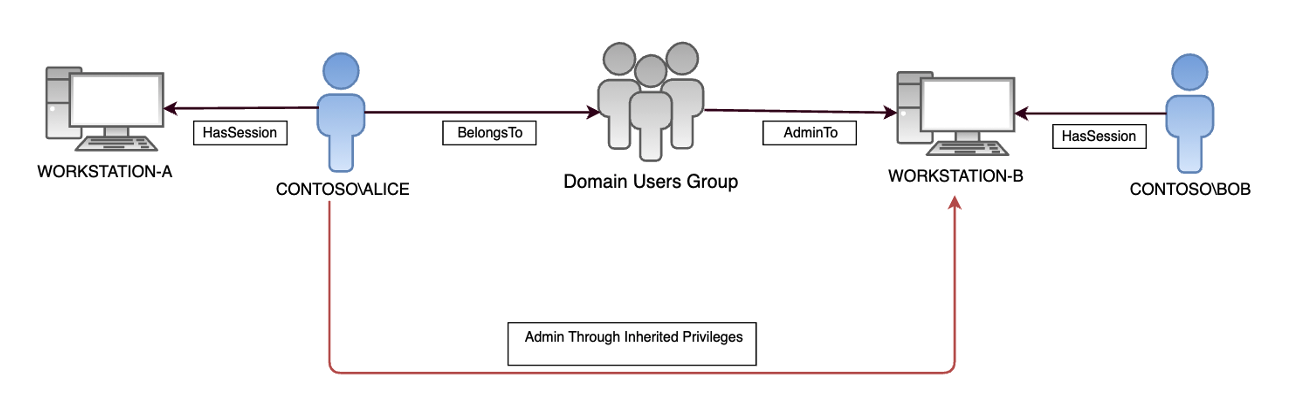
![Pentester Academy] Attacking and Defending Active Directory Free Download Pentester Academy] Attacking and Defending Active Directory Free Download](https://courseclub.me/wp-content/uploads/2019/07/4564555.png)